16 Ways to Strengthen WordPress Website Security
Contents
Contents
WordPress’s popularity has an unfortunate side effect of the WP websites making a desirable target for malicious attacks. It might make you wonder if WordPress is secure enough to handle them. A short answer would be: “It depends.” A more in-depth explanation is that WordPress is a relatively safe platform, but there is no such thing as a 100% secure website. Often, the best approach is to protect your site against the largest and most common threats.
Among the most common threats are backdoors, brute-force login attempts, malicious redirects, and cross-site scripting (XSS). Let’s take a quick look at each of them.
- Backdoor attacks
As one can guess from its name, backdoors are hidden paths that allow hackers to intrude into the control panel using wp-admin, FTP, or other methods. Reports say that backdoor attacks compose almost 80% of all malicious actions on WP sites. - Brute-force login attempts
In this case, hackers launch automated scripts to test websites for weak passwords and break down those they find. Although a remedy for this type of attack is quite obvious — a strong password — almost 30 000 websites become victims of brute-force login attempts daily. - Malicious redirects
If hackers can’t find a backdoor on their own, they launch a malicious redirect to create one. If the attack is successful, your website traffic will be redirected to a malicious site. - XSS
Finally, cross-site scripting, another wide-spread type of attack, enables hackers to inject client-side scripts into the websites. By doing so, they receive access to valuable information like panel control or cookies.
Is it safe to use WordPress?
Let’s be clear. WordPress websites indeed become victims of malicious attacks more frequently than websites created with other technologies. According to the Sucuri report, more than 80% of infected or hacked websites were built on WordPress. In contrast, other platforms like Joomla, Magento, or Drupal, demonstrate sufficiently lower percentages — 13%, 6%, and 1,6% accordingly.
But these worrying numbers have a straightforward statistical explanation. Many WP websites are getting attacked just because of the platform’s popularity — almost 40% of all sites on the Internet are WordPress-based. Another reason is that users frequently dismiss basic security practices to protect their websites.
In this article, we will look at the most waterproof tools and techniques to keep your WordPress website safe and sound.
Invest in secure WordPress hosting

The path towards WordPress security begins with choosing a reliable host. Your host should have several layers of hardware and software security measures to protect your website from potential attacks. While there are thousands of providers out there, the official WordPress website has already done the hard work for you and chosen three waterproof hosts:
- Bluehost. Armed with top-notch WordPress-centric dashboards, Bluehost powers more than 2 million websites, and yours can become one of them without hesitation.
- DreamHost. The name of this host speaks for itself. It has been powering WordPress websites for 10 years, actively contributing to the worldwide WordPress community.
- SiteGround. With lots of useful tools for managing WP websites and a 24/7 support team, SiteGround is another fabulous option for your next host.
If you want to use your own VPS for hosting, then you must be confident your tech capacity is enough to arrange all security measures. Fast Ubuntu servers are another solid choice for maximizing speed and security while handling site demands efficiently. Pay attention to the available server-level and hardware firewall options, reliable backup systems, and uptime monitoring while avoiding FTP connections. We suggest choosing proven hosts with the latest operating systems, which can detect attacks and block them if needed.
Turn on automatic updates
Having the latest updates is essential to keep your website safe. However, users can forget to install updates or postpone them “till Monday”, putting their websites at risk. But there is a simple way to overcome this problem — turn on automatic WordPress plugin or theme updates and enjoy your latte while the CMS does the work for you. While it is better to hire a specialist who can set up automatic updates, you can also do it yourself to ensure WordPress security.
-
- To turn on automatic WordPress updates, follow instructions on the official WordPress website. Just keep in mind that it requires decent tech skills and a few website backups.
- If you want WordPress to automatically install all plugin updates automatically, then add this code to your theme’s functions.php file or a site-specific plugin.
add_filter( 'auto_update_plugin', '__return_true' ); - In case you’d like automatic updates of your themes as well, add this code:
add_filter( 'auto_update_theme', '__return_true' );
WordPress recently added the option to auto-update plugins and themes. If your site’s version is 5.5 or later, you can go to the Plugins page and turn on auto-updates for individual plugins. Similarly, you can auto-update particular themes on the Themes page.
Still, be sure you understand what you are doing. Experienced WordPress developers know how painful it is to update a plugin or theme and break the website. To avoid this mishap, consider only enabling auto-updates for plugins and themes that haven’t caused problems before or those that won’t directly affect what gets rendered on pages.
Use the latest PHP version
We’ve already mentioned your website host should have the latest operating system updates to ensure site security. Unsurprisingly, so does your PHP version. PHP is like social media for the Kardashians — essential for the website’s success. Traditionally, a new version of PHP is released every two years. Therefore, if you’ve had a website, say, for three years now, you should’ve updated your PHP version at least once. Having the latest version is crucial. Not only do they work better, but developers fix vulnerabilities in older versions regularly. If you refuse to reap the benefits of their work, there is a good chance that hackers can use those vulnerabilities to break into your site.
Unfortunately, almost 80% of websites are still running on outdated and unsupported PHP versions. If you find yourself among this reckless pack, install the latest PHP version immediately. WordPress recommends having PHP version 7.4 or greater, which can be installed by following these detailed instructions. But, hey, PHP is not the only kid on the block. You can also install MySQL version 5.6 or greater, or MariaDB version 10.1 or greater. Just don’t forget to make a backup of your site and check the new version’s compatibility.
Disable directory listing
Directory browsing means any user can get into your directory, check your files, and browse through folders. From a security standpoint, this entire scenario looks quite disturbing. In fact, newer versions of WordPress already have default safety measures against directory browsing. However, some plugins haven’t followed suit, so you can still have activated directory listing even on the newest WP versions.
The best way to disable directory browsing is to add the following line of code to a .htaccess file:
Options - Indexes
If you use NGINX, the directory listing is disabled by default.
Disable XML -RPC pingback
Previously, XML -RPC had many beneficial features like allowing users to write content offline and then publish it on their WordPress sites. In other words, it enabled any remote device or app to send data to your website. But that was in the days prior when the internet was young and innocent. Today, this feature jeopardizes your WordPress security since each pingback exposes your website access to malicious attacks. WordPress sites developed after 2015 have this option turned off by default, so you should be safe with a WP version of 4.4.1 or greater. Still, some plugins continue using XML -RPC pingback today – Jetpack is one of the most popular ones.
To ensure your website is secure, double-check it by going to Settings > Writing > Remote Publishing. If you find one of your plugins has activated the XML -RPC pingback, you can pull it by installing Disable XML -RPS plugin.
Another way to remove the pingback is to copy/paste the following code to functions.php:
// disable pingbacks
add_filter( 'xmlrpc_methods', function( $methods ) {
unset( $methods['pingback.ping'] );
return $methods;
} );
To be sure the pingback was disabled, you can use an online validation tool like this one.
Add latest HTTP security headers

Anytime a user visits your website via a browser, the server launches an HTTP response header. These headers instruct the browser how it should act when interacting with your website. By using the latest HTTP security headers, you can teach browsers good manners and tell them to treat your website with caution and dignity.
For instance, if you add HTTP Strict transport security, you will make all web browsers access your website with HTTPS only. X-XSS protection will keep your site safe from cross-site scripting. X-Frame options will provide clickjacking protection by not allowing other sites to embed content from yours.
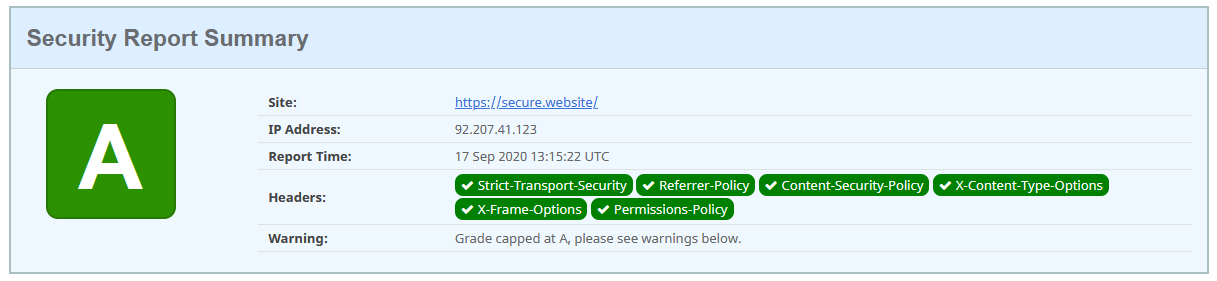
Use this resource to see if your website meets security requirements, and this one to add HTTP security headers.
Pay attention to file permissions
Another step in improving WordPress security is finding the right balance in files and directory permissions. Having too many permissions creates fertile soil for malicious attacks. On the other hand, having too strict permissions disrupts the entire system’s work. Make sure files and directories meant only for reading have nothing more than read-permissions. Simultaneously, give execute-permissions only to users who need to modify files or perform functions and commands.
WordPress recommends the following file and folder permissions:
- Folders – 755 or 750
- Files – 644 or 640
- wp-config.php – 440 or 400
- .htaccess – 644, or 600
For example, folder permission of 750 means:
The administrator has permission to read, write, and execute
Other users, like editors and contributors, have permission to read and execute only
The remaining internet users have no access at all.
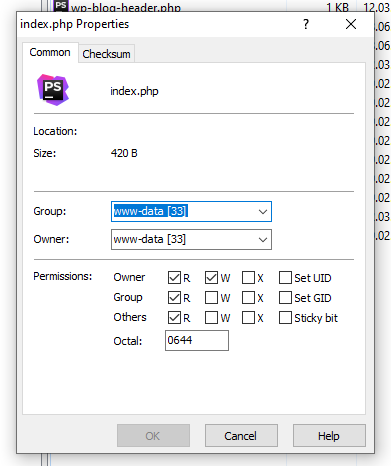
For more in-depth information on how file permissions work, check out this article.
Use different roles for users
A standard WordPress website has six defined roles: super-admin (for multisite setup), administrator, editor, author, contributor, and subscriber. These roles differ by the extent to which users can exploit the dashboard and modify the website. No matter how tempting it might be to assign each co-worker, family member, and random delivery guy with a super-admin role, you probably shouldn’t. It’s better to keep this role to yourself and give other users less significant roles like authors or editors, depending on how they interact with the website.
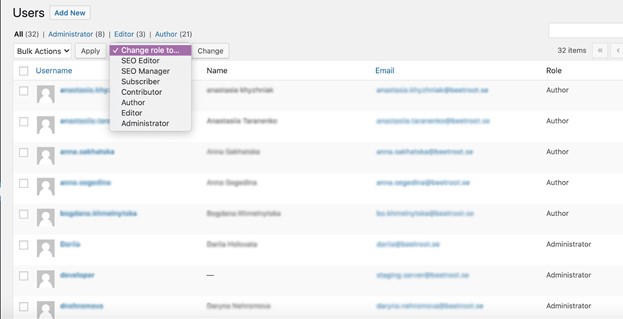
You can also change the capabilities of standard roles by changing the code or using plugins. By doing so, you will limit the number of people who can make changes to the website’s essential functionality while adding to your WordPress security.
Website firewalls
Think of a beefy bouncer who had the audacity not to let you into a high-end party because you were wearing cargo shorts – firewalls have similar functionalities. They act as a bouncer between the internal network and outside, potentially dangerous inquiries. They control who can access the network and monitor incoming internet traffic.
There are three ways to strengthen your website with firewalls.
First, you can install any of the WordPress firewall plugins, which are easy to set up. However, if your website had a vulnerability before the plugin was installed, it won’t be protected entirely. In general, those plugins step in between your website and all incoming traffic, blocking the threats before the loading is triggered. The best plugins in this category are Sucuri Security, MaxCDN (by StackPath), Cloudflare, Wordfence Security, Jetpack, and BulletProof Security.
Second, you can use the WordPress web application firewalls. Unlike plugins, they are installed between your website and the internet connection versus specifically on your website. This approach makes them a more secure option than plugins. But the downside of using WAF is they are quite expensive.
Finally, you can use an online WordPress website firewall. It has many advantages and can be used as a firewall and as a cache server and CDN. However, having an online firewall won’t make your website utterly invisible to malicious attacks. Hackers will still be able to communicate with your web server if they know its IP address. Cloudflare and Sucuri are the best options if you decide to choose a WAF or online WordPress website firewall.
Strong password
Good health starts with clean hands and a nutritious diet; WordPress security starts with a strong password. Sounds pretty obvious, right? But before you skip this paragraph, we want to share something interesting with you. According to the SplashData report, most websites broken over the past year had passwords like “123456” or the ludicrous word “password” itself. Think about it – while we all seem to know websites should have strong passwords, there are still people who use obvious passwords to protect their sites. While you may never make such an erratic mistake, here is the link to Strong Password Generator, just in case.
Strengthen your databases
There are several ways to ensure WordPress security with the help of databases. To start with, think of a complex and non-obvious name for your database. If your website is called All Dogs Are Beautiful, your database will be named wp_alldogsarebeautiful by default. While it might be tempting to leave it as is, such a simple database name is low-hanging fruit for hackers. Try something more challenging like wp_frank. You can even go one step further and change the database table prefix. Instead of wp_frank, your database can be 57wp_frank, which automatically promotes you to the “evil genius” security level.
With databases, you can also restrict user privileges. For instance, If you have several WordPress setups on the same web server, create separate databases with limited user access. In case one of your databases is hacked, others will have a better chance to stay safe.
For regular operations on WordPress websites, like blog posting or uploading images, users need only privileges for data operations. In other words, they should be granted the following specific database privileges: SELECT, INSERT, and UPDATE. The remaining privileges concern structure and database administration, which most users don’t need regularly. However, some plugins might require additional database privileges such as CREATE, DROP, or DELETE, which can be granted temporarily and then revoked.
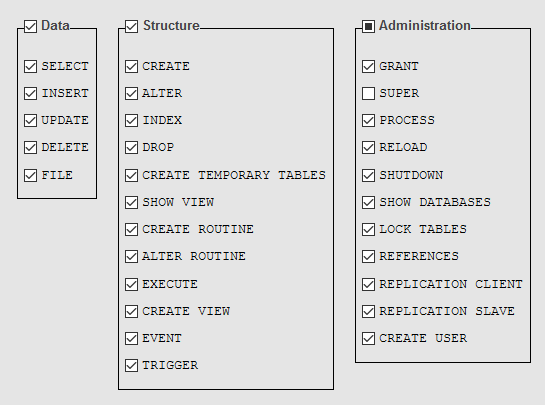
For more information, check out the official MySQL documentation.
Setup SSL and HTTPS
There is a general misconception that HTTPS is only needed if you’re running an e-commerce website and accept credit cards. However, having an HTTPS can be a real game-changer in protecting any WordPress site.
- First, even if you don’t collect users’ card numbers, HTTPS will give you a secure connection between your website and browser, minimizing the risks of your data being intercepted.
- Another advantage of using HTTPS is that Google loves it. According to Webmaster Central Blog, HTTPS is an SEO ranking factor.
- Finally, having an “https” in the address bar will most likely make your website look reliable and trustworthy in the eyes of users. At least, that’s what GlobalSign’s report says – 77% of users are concerned about their personal data being intercepted on an “http” website.
With that said, follow these instructions to set up SSL and HTTPS in a matter of minutes.
Make backups regularly
You must’ve heard at least once that backups are important. But, honestly, how often do you actually take time for them? Despite all possible excuses, try to make at least three backups on a regular basis.
WordPress offers several services and plugins to help you make and store backups. Here you can read guidelines for completing manual and automatic ones. You can also check with your hosting provider for details on what you can do to backup your site. If you have time and resources, you can even set it up on your own. If not, it’s better to entrust it to tech experts.
Disallow file editing

As mentioned above, it might not be a good idea to grant super-admin access to those who can get the job done with a more specific role like “author” or “contributor.” If you are a risk-taker, though, and choose to keep seventeen super-admins in your control panel, make sure you disallow file editing to secure your WordPress site.
WordPress automatically gives theme and plugin editing access to every dashboard administrator. However, if you never change files on your website directly, you can simply disable this feature. Here’s how:
-
- Search for the setting
DISALLOW_FILE_EDITin wp-config.php - Add the following line:
define('DISALLOW_FILE_EDIT', true); - If you’ve never completed this before, the setting will not be there. You will need to add this string after the
WP_DEBUGline.
- Search for the setting
Two-factor authentication

Even if you follow all of the instructions we suggest, it’s still wise to set up two-factor authentication to be safe. With this in place, your website will be protected not only by a password, but your identity will also be verified by any action you choose: an SMS-code, a phone call, or a passcode. This step creates another barrier for hackers, who will now need to take over your password and your cellphone to get into the control panel.
Shuffle SALTs
If you want to stay logged in, WordPress saves your email, username, and password information in cookies. It’s convenient, no doubt, but it can be somewhat risky from a security standpoint.
To keep you both logged in and safe, WordPress uses SALTs and security keys to strengthen your password. These measures turn your password into a set of random characters so that no hacker can sink their teeth into your personal info.
By default, WordPress security keys and SALTs are located in the wp-config.php file and look like this:
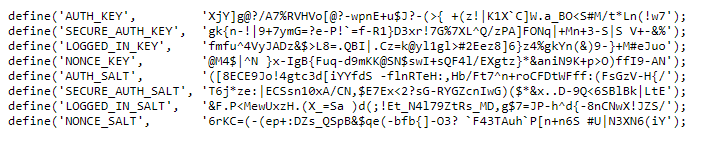
However, it would be best if you shuffled them from time to time to prevent malicious attacks and ensure your WordPress admin panel remains secure.
You can change SALTs manually by editing your wp-config.php file or using a special plugin. The new SALTs can be taken from the official WordPress.org salt generator, replacing the existing keys in your wp-config.php file with the newly generated ones. If you prefer not to change it manually, use a Salt Shaker plugin and save the extra time for yourself.
Summary
So, where does this leave us? The majority of WordPress security practices are quite intuitive and easy to implement. Having a secure host, enabling two-factor authentication, creating strong passwords, and watching over the control panel roles will help you ensure a secure site. Yet, these steps are often overlooked, which puts thousands of websites around the world at risk. Be sure to follow our simple instructions for keeping your website secure and well-functioning.
And, if all of the above instructions seem a bit overwhelming, you can always hire professional WordPress developers who will help keep your website safe and sound.
Subscribe to blog updates
Get the best new articles in your inbox. Get the lastest content first.
Recent articles from our magazine
Contact Us
Find out how we can help extend your tech team for sustainable growth.