Green Cybersecurity: Sustainability in Data Protection
Contents
Contents
As we are nearing the end of 2024, marked by some of the most devastating security breaches in recent history, the need for reliable cybersecurity services has never been higher. From massive leaks of customer personal information to the unprecedented theft of medical data affecting most U.S. residents, this year’s data breaches have surpassed 1 billion stolen records and continue to rise. Meanwhile, in the U.K., 50% of businesses and a third (32%) of charity organizations reported some form of cybersecurity breach or attack they experienced in the last 12 months (as of July 2024).
Amid this shifting threat landscape, cybersecurity has become a fundamental part of business operations. Yet, expanding cybersecurity infrastructure on this scale has notable environmental consequences. Enter green cybersecurity — a new approach that integrates robust data protection with a commitment to sustainability.
Why Green Cybersecurity Matters in Data Protection
With the world becoming increasingly dependent on connected systems, there is a pressing need to ensure the security and integrity of digital technologies. Rather than an option, sustainable cybersecurity practices are becoming a necessity as organizations face the dual challenge of securing digital assets and meeting sustainability goals.
Three critical factors drive the shift toward sustainable cybersecurity:
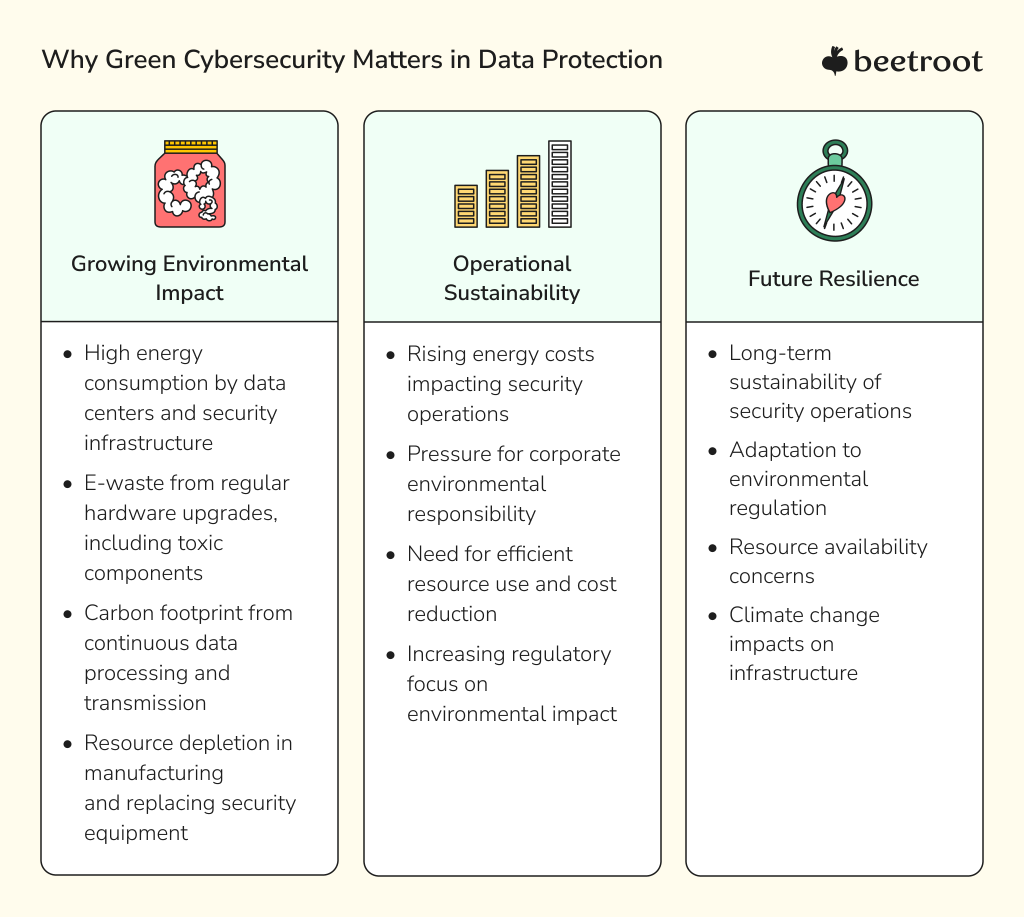
The environmental impact of traditional cybersecurity practices is substantial and growing. Data centers, which form the backbone of modern cybersecurity infrastructure, consume between 1-2% of global electrical power – a figure that continues to rise as digital transformation accelerates. This energy consumption is primarily driven by two factors:
- The power required to operate servers and security infrastructure
- The energy-intensive cooling systems necessary to maintain optimal operating temperatures
The rapid evolution of cybersecurity technology creates another pressing environmental challenge: electronic waste. In their race to defend against emerging threats, organizations frequently replace outdated hardware with newer systems. Beyond the sheer volume of discarded equipment (and yes, it still can be hacked), this e-waste poses serious environmental risks, as its toxic components can leach into the soil and contaminate water sources when not properly handled.
By adopting green technology solutions, companies and organizations can address both security and sustainability challenges simultaneously. This approach isn’t just environmentally responsible – it’s becoming a business imperative as customers and stakeholders increasingly prioritize sustainability.
Defining Green Cybersecurity: A Holistic Approach
Green cybersecurity refers to practices and technologies designed to be secure and eco-friendly, an intersection of data protection and environmental responsibility. By emphasizing sustainability in the development and operation of security infrastructure, this approach seeks to reduce the carbon footprint of cybersecurity operations without compromising protection against cyber threats.
Pillars of Green Cybersecurity
Sustainable Hardware
Green cybersecurity begins with hardware optimized for both performance and sustainability:
- Low-power processors, such as those based on ARM architecture, deliver high performance with reduced energy use.
- Solid-state drives (SSDs) consume less power and generate less heat than traditional drives.
- Modular systems allow for component upgrades rather than complete replacements, reducing electronic waste.
- Energy-efficient networking equipment with power management capabilities further reduces consumption.
Energy-Efficient Data Centers
Modern eco-friendly data centers are central to green cybersecurity by incorporating:
- Advanced cooling technologies, like liquid and free-air cooling, to reduce energy demands.
- Renewable energy sources, such as solar, wind, or hydroelectric power, to offset carbon footprints.
- Smart grid technologies for optimized power distribution and efficiency.
- LEED-certified designs and waste heat recovery systems for energy-efficient operations.
Optimized Software and Algorithms
On the software side, green cybersecurity emphasizes efficiency and resource optimization:
- Efficient code design to reduce computational demands.
- Automated resource scaling to align resource use with demand dynamically.
- Data compression and storage algorithms that optimize storage use.
- AI-powered optimizations in security operations for streamlined performance.
- Cloud-native security solutions that enhance resource utilization in distributed environments.
This approach marks a paradigm shift in data protection as organizations blend robust security measures with a commitment to sustainability. Green cybersecurity is not just a set of technologies; it integrates sustainable practices into the innovation, implementation, and operation of cybersecurity systems.
Concepts and Benefits of Eco-Friendly Cybersecurity
Green cybersecurity addresses the environmental impact of traditional practices, which often prioritize protection at any cost. This “more is better” approach leads to oversized infrastructure and resource-intensive operations. In contrast, green cybersecurity aims to deliver robust protection while minimizing environmental footprint.
Environmental Responsibility in Security Operations
Environmental responsibility in cybersecurity begins with infrastructure planning and extends through the entire security lifecycle. Organizations must consider not only the immediate security requirements but also the long-term environmental implications of their security decisions.
For instance, when planning security infrastructure, companies traditionally focus on maximum capacity requirements, often leading to substantial overprovisioning. A green cybersecurity approach instead advocates for scalable solutions that can adapt to varying security needs while minimizing resource waste. This might include implementing dynamic resource allocation systems that can adjust security measures based on actual threat levels and operational requirements.
Sustainable Security Architecture
The concept of sustainable security architecture represents a fundamental shift in how we design and implement security systems. Rather than treating environmental considerations as an afterthought, they become integral to the security design process. This integration requires careful consideration of how security measures impact energy consumption, resource utilization, and overall environmental footprint.
For example, when designing security monitoring systems, a sustainable approach might focus on optimizing data collection and analysis processes to reduce unnecessary processing and storage. This could involve implementing smart filtering systems that prioritize relevant security data while minimizing the resources spent on processing low-value information.
Green Cybersecurity Benefits in the Climate Change Era
While green cybersecurity is still an emerging field, several potential benefits are beginning to emerge as organizations experiment with more sustainable security practices.
Environmental Impact Reduction
The most direct potential benefit lies in reducing the environmental impact of security operations. By integrating sustainability considerations into security practices, organizations may find opportunities to:
- Optimize energy consumption through more efficient security infrastructure
- Reduce electronic waste by extending hardware lifecycles where security requirements permit
- Minimize unnecessary data processing and storage, reducing the resources required for security operations
- Implement more efficient cooling solutions for security infrastructure
However, it’s important to note that these benefits are often interconnected with broader organizational sustainability initiatives and may be difficult to attribute solely to security practices.
Operational Advantages
Beyond environmental benefits, companies implementing sustainable security practices may discover operational advantages. While specific outcomes will vary depending on implementation and context, potential advantages include:
- More efficient resource utilization leading to optimized operational costs
- Better integration with organizational sustainability goals and reporting
- Improved alignment with emerging environmental regulations
- Enhanced infrastructure longevity through optimized resource use
These advantages often emerge as part of broader organizational transformation efforts rather than as immediate results of specific security changes.
Green Cybersecurity Practices
While no standardized framework yet exists for green cybersecurity, several key practices are emerging that organizations and businesses can consider as part of their journey toward more sustainable security operations.
Infrastructure Optimization: Beyond Energy Efficiency
The foundation of sustainable security practices begins with infrastructure optimization, extending beyond basic energy efficiency to encompass the entire lifecycle of security systems. Traditional security infrastructure, with its “better safe than sorry” approach, often maintains redundant systems at full capacity. While redundancy remains crucial for security, organizations are beginning to explore more nuanced approaches. As we mentioned earlier, some are implementing adaptive security systems that can adjust security measures based on threat levels and operational needs, reducing unnecessary resource usage.
The role of data centers in security operations deserves particular attention. While many organizations are familiar with green data center practices, applying these principles specifically to security infrastructure presents unique challenges. Security systems often require real-time response capabilities and continuous monitoring, making it more complex to implement power-saving measures without compromising protection. However, innovative approaches are emerging, such as:
- Intelligent workload distribution that considers both security requirements and energy efficiency
- Advanced cooling systems specifically designed for security infrastructure
- Smart power management systems that maintain critical security functions while optimizing energy use
- Modular security architectures that allow for more efficient resource allocation
Operational Transformation: Rethinking Security Processes
The transition toward sustainable security practices touches every aspect of security management, from daily monitoring practices to incident response procedures. Traditional security monitoring often operates on the principle of “collect everything, analyze later.” This approach, while thorough, leads to massive data storage requirements and significant processing overhead. A more sustainable approach might involve:
- Intelligent data filtering that prioritizes high-value security information
- Real-time analysis that reduces storage requirements
- Adaptive monitoring systems that adjust their scope based on threat levels
- Efficient data lifecycle management that balances security needs with resource usage
However, implementing these changes requires careful consideration of security implications. Organizations must ensure that any reduction in data collection or monitoring scope doesn’t create security blind spots or compromise their ability to detect and respond to threats.
Risks and Challenges in Implementation
The integration of sustainability considerations into security infrastructure presents several technical and organizational challenges that companies must address to maintain security effectiveness while pursuing environmental goals:
Performance and Protection Balance
One of the most significant challenges lies in maintaining robust security while implementing more resource-efficient practices. Security systems often require rapid response times and continuous monitoring, making it difficult to implement power-saving measures without potentially compromising protection. Organizations must carefully evaluate how efficiency improvements might impact:
- Threat detection capabilities
- Response times for security incidents
- System availability and reliability
- Data processing and analysis capabilities
These considerations require a delicate balance between environmental goals and security requirements, often necessitating innovative solutions that can satisfy both needs simultaneously.
Integration Challenges
Existing security infrastructure rarely exists in isolation. Most organizations have complex security ecosystems that have evolved over time, often incorporating multiple layers of protection and various security technologies. Introducing sustainability considerations into these established systems presents several challenges:
- Compatibility issues between new, efficient solutions and existing security tools
- Complex dependencies that make changes to any single component risky
- Legacy systems that may not support more efficient operating modes
- Integration requirements with broader organizational systems
Mindset and Priorities
Beyond technical challenges, organizations often face significant internal barriers to implementing sustainable security practices. Security teams have traditionally operated with a singular focus on protection, often viewing any other considerations as potential compromises to security. Shifting this mindset to include environmental impact as a valid consideration requires significant cultural change:
- Education about the relationship between sustainability and security
- Development of new evaluation criteria for security measures
- Changes to decision-making processes
- Evolution of security policies and procedures
Future of Green Cybersecurity and Sustainability in Tech
The evolution of green cybersecurity represents a sophisticated balance between advancing security needs, environmental goals, and innovative technologies. As organizations strive for sustainable security practices, several specific trends and technological shifts are emerging that will shape the future.
Industry 4.0 and Cyber-Physical Security
Industry 4.0 technologies, such as IoT, smart factories, and cyber-physical systems, create both opportunities and challenges for sustainability and transform industrial security practices. In smart manufacturing environments, for example, massive data volumes require robust protection, yet these same systems can help optimize resource use. AI-driven monitoring can enable security protocols to adjust in real-time, ramping up protection during periods of increased risk and conserving energy when threats are minimal.
Moreover, the convergence of operational technology (OT) and information technology (IT) within Industry 4.0 frameworks allows for integrated security solutions that safeguard both digital and physical assets. For instance, predictive security measures in OT environments can reduce energy-intensive monitoring activities by prioritizing risks based on patterns and historical data, thus optimizing resource use across entire facilities.
Artificial Intelligence and Resource-Efficient Security
Emerging green cybersecurity approaches focus on designing AI algorithms that balance processing power and efficiency. This might involve more sophisticated, lightweight algorithms capable of real-time threat detection without excessive computational demands. For example, AI-based intrusion detection systems can be optimized to function in lower-power modes during low-risk periods, switching to full-capacity operation only when anomalies are detected. Additionally, advancements in federated learning could reduce the need for centralized data processing by enabling local analysis and response, thus reducing both latency and energy use.
Evolving Infrastructure for Sustainable Security
The physical infrastructure of cybersecurity, including data centers and edge computing, is evolving to incorporate more energy-efficient solutions. Modern data centers are increasingly adopting renewable energy sources and advanced cooling methods like liquid cooling and free-air cooling, reducing overall power consumption. Additionally, modular data center designs allow for scalability, so organizations only use the resources they need, minimizing energy waste.
Edge computing is gaining prominence in sustainable security, as it allows data to be processed closer to its source, which can significantly reduce the energy footprint associated with long-distance data transmission. Security protocols at the edge can prioritize local data analysis for faster, more energy-efficient threat detection, although this requires carefully coordinated security across decentralized infrastructures to ensure consistent protection.
Regulations and Standards for Sustainable Cybersecurity
As awareness of cybersecurity’s environmental impact grows, regulatory bodies are beginning to establish standards for green cybersecurity. These may include guidelines on emissions tracking, energy use, and reporting frameworks that align cybersecurity practices with broader sustainability goals. New certifications for green cybersecurity practices could emerge, setting benchmarks for energy-efficient operations, use of renewable energy, and lifecycle management of hardware and software. Organizations complying with these standards will likely benefit from reduced costs and enhanced reputational value as sustainability becomes an expected component of corporate responsibility.
Green Cybersecurity: Industry Implementation Approaches and Case Studies
The practical application of green cybersecurity varies across industries, as each sector faces unique challenges and opportunities. The following are potential use cases and implementation approaches that highlight how sustainable security practices can be tailored to industry-specific needs.
Financial Services Sector
The financial services industry operates under stringent security and regulatory requirements, making it challenging to implement green cybersecurity solutions without compromising compliance. However, financial institutions can adopt sustainable practices in the following ways:
- Infrastructure optimization: Banks and financial institutions can enhance security operations by implementing more energy-efficient monitoring systems while meeting regulatory standards. By optimizing data center operations specifically for security workloads, they can reduce power consumption. Additionally, transitioning to cloud-based security solutions can lower the environmental impact by utilizing cloud providers committed to renewable energy.
- Sustainable disaster recovery and business continuity: Financial services can develop environmentally friendly disaster recovery strategies. For instance, cloud-based disaster recovery services can be designed to consume fewer resources during non-disaster periods, only scaling up when active data protection is required. This approach not only conserves energy but also minimizes infrastructure redundancy.
- Operational balancing of compliance and resource efficiency: Financial organizations must balance real-time security needs with compliance obligations (such as those set by GDPR or PCI DSS) while optimizing resources. AI-based security solutions that adjust processing power based on immediate needs can help maintain compliance and data protection without excessive energy use.
Healthcare Industry
In healthcare, the priority on patient data protection and HIPAA compliance creates unique challenges for sustainable security. Green cybersecurity in this sector can focus on balancing robust protection with energy efficiency:
- Efficient Electronic Health Record (EHR) security: Implementing optimized security solutions for electronic health records can reduce the resource demands of constant data access and monitoring. For instance, AI-driven threat detection that only activates higher processing power when anomalies are detected can minimize energy use during routine access.
- Sustainable medical device security: Medical devices connected to hospital networks require secure and continuous monitoring. Sustainable cybersecurity for these devices could involve lightweight, energy-efficient encryption and monitoring solutions that are less resource-intensive but still meet compliance and data protection requirements.
- Resource-conscious data protection systems: As healthcare systems handle vast amounts of patient data, implementing data protection measures that rely on renewable-powered data centers or energy-efficient storage can mitigate environmental impact. This approach is particularly valuable for large health networks where data storage and transfer demands are substantial.
Manufacturing Sector
In manufacturing, operational technology (OT) environments and industrial control systems (ICS) are critical, with security implications that extend to physical infrastructure. Sustainable security practices in this sector focus on optimizing the protection of cyber-physical systems while conserving resources:
- Industrial Control Systems (ICS) security: Manufacturing organizations can secure their industrial control systems with energy-efficient solutions that protect against cyber threats without heavily taxing the OT environment. This might involve AI-based threat detection that dynamically adjusts monitoring levels based on the assessed risk, thus conserving energy during lower-risk periods.
- Sustainable security monitoring for production environments: Real-time monitoring of production environments is essential for detecting cybersecurity threats, but continuous operation can consume significant resources. Manufacturers can implement green cybersecurity by optimizing network and device monitoring protocols to operate in low-power modes unless suspicious activity is detected.
- Environmental impact of security infrastructure: Manufacturing companies can reduce the environmental footprint of their security infrastructure by deploying resource-efficient hardware and renewable energy sources for sustainable data storage and processing. By shifting data-intensive security tasks to renewable-powered data centers, they can secure critical operations while minimizing environmental impact.
Conclusion: Embracing a Sustainable Security Future
The evolution of cybersecurity toward more sustainable practices represents a fundamental shift in how organizations approach digital protection. As we’ve explored throughout this discussion, this transformation goes beyond simple technology changes to encompass new ways of thinking about security, sustainability, and their intersection in modern business operations.
The path forward requires ongoing commitment to learning, adaptation, and innovation. By prioritizing both security and sustainability, organizations can help create a future where robust digital protection coexists with environmental responsibility. This is not just a technical challenge but a fundamental requirement for sustainable development in our increasingly connected world. Success in this endeavor depends not only on implementing appropriate technologies and practices but also on developing the right expertise and mindset within security teams.
The role of continuous learning and skill development cannot be overstated in this context. Through specialized training programs offered by Beetroot Academy, your teams can develop the unique combination of security expertise and sustainability awareness needed in this evolving landscape. Our expert workshops, designed for both technical and non-technical specialists, help build the foundational knowledge and practical skills required to implement and maintain effective sustainable security practices in your business.
Ready to contribute to a more sustainable and secure digital future? Contact our experts to explore how your organization can implement security practices that protect both your digital assets and our shared environment.
Subscribe to blog updates
Get the best new articles in your inbox. Get the lastest content first.
Recent articles from our magazine
Contact Us
Find out how we can help extend your tech team for sustainable growth.